The Volatility Team is very proud and excited to announce the first official release of Volatility 3 that can not only fully replace Volatility 2 for modern investigations, but also with many new and exciting features!
In this blog post we document many of these new features, give a quick tour of Volatility 3 itself, and provide links to many resources that will help analysts get up to speed on bleeding-edge memory forensics techniques and capabilities.
With this official release of Volatility 3, Volatility 2 is now deprecated, and the GitHub repository has been archived.
AT A GLANCE
- Volatility 3 has reached feature parity; Volatility 2 is now deprecated.
- Volatility 3 supports the latest versions of Microsoft Windows and Linux.
- Volatility 3 has many brand new plugins and features never available in Volatility 2.
- Volatility 3 will be actively supported for many years.
- The Memory Analysis | Malware and Memory Forensics Training course has been completely updated to focus on Volatility 3.
The History of Volatility and Motivation for Volatility 3
First presented in the form of VolaTools at Black Hat 2007, Volatility has since become the mostly widely used open-source memory forensics framework. The second version of the framework, Volatility 2, has been the long-standing major version of the framework and provided many innovative features for analysts performing investigations ranging from insider threat to malware analysis to proactive threat hunting.
As the scale and scope of modern investigations changed, with individual systems moving from as low as 512MB or 1GB of RAM by default to now many gigabytes with standard investigations involving dozens of systems, the initial design of Volatility 2 started to strain. The wide-ranging user base also requested many features over the years, such as generic output formats, default timeline integration, and plugin harnesses, that would have been hard to envision and design for in 2007.
See the complete history of the Volatility Framework in a detailed timeline!
To rectify this situation and update Volatility to meet the wide-ranging needs of modern investigations, Volatility 3 was designed from scratch with scalability, ease of use, and long-term, flexible APIs in mind. This architecture and design effort was led by Mike Auty (@ikelos) and has brought Volatility 3 to where all of the pain points of users and developers of Volatility 2 were fixed from the beginning.
Highlights of this effort include removal of the ‐-profile argument requirement for all operating systems, the automatic timeline integration of all plugins that produce timestamps, and extensible structured output formats, with automatic support for all plugins as they are added to the framework. These features, along with the ‐-filters feature discussed later, have received very positive feedback in our recent workshops and trainings based on Volatility 3.
New Features in Detail
In this section, we will highlight just a few of the most useful and highly rated new features of Volatility 3. Complete project documentation is added to our Read The Docs site on an ongoing basis, and we gladly accept quality documentation contributions from contributors outside of the core team.
No More ‐-profile!
The feature that all users rejoice over is the removal of ‐-profile from Volatility 3. Instead of relying on user input to determine the operating system type, Volatility 3 can determine the specific operating system version on its own, leading to more accurate results and unlocking the ability to script analysis over many plugins and memory samples.
For Windows, this processing happens automatically if the analysis system is online and can reach Microsoft’s symbol servers. For offline Windows users, or for analysis of Linux systems, please see the Read The Doc links for adding support and automation.
The ‐-filters Flag
Even command-line wizards often found it difficult to properly filter Volatility 2’s output using tools like grep and awk. This was especially true when attempting to search for specific numbers across plugins that produced several numeric columns and when searching for very short strings.
Thankfully, users no longer need to worry about this due to the addition of the ‐-filters flag. With this feature, users can specify one or more columns to automatically search inside of, and only rows matching at least one filter will be produced. The search term can be a simple string, full regular expression, or a numeric value.
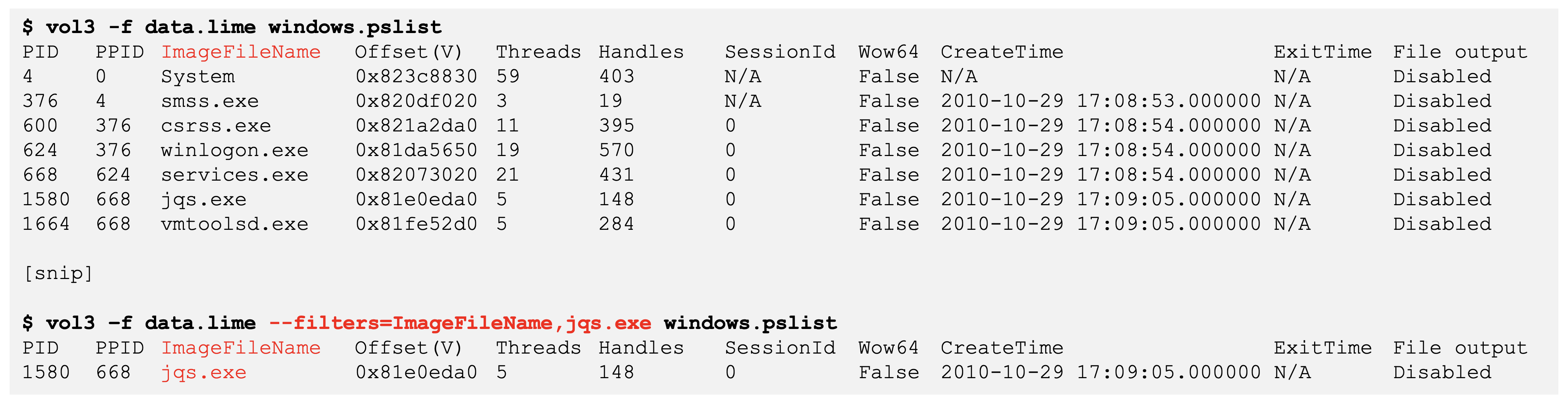
The following figure shows a slide from our training class where the ImageFileName column of windows.pslist is filtered to only entries containing jqs.exe. The slide also includes notes at the bottom for varying input formats.
As mentioned previously, the ‐-filters flag also supports numeric values as shown in the screenshot below when listing memory ranges (VADs) starting at address 0x1000000:

In this example, the Start VPN column is being filtered by its address in hex. With Volatility 2 and grep, this number could have partially or fully matched any column, leading to the inclusion of unwanted output. With Volatility 3, only the specified column is searched, and only for the specified value.
We strongly encourage users to experiment with and learn this feature, rather than using imprecise filters based on piping Volatility’s output through an operating system’s built-in filtering tools.
Generic Output Formats, including Aligned Tables
In Volatility 3, the default output renderer will produce rows as a plugin generates them and will have varying column width per row, the same as Volatility 2. This can be very hard to read, as column values can interleave. In the screenshot above, the metadata of the VADs being displayed was very easy to read due to Volatility’s aligning of the output according to column length. This alignment occurred due to the specification of -r pretty on the command line.
Due to Volatility 3’s design, all plugins support all output formats generically. At the time of writing, besides the default quick and pretty, output options include csv, json, and jsonl. If you wish to contribute your own output format, then see volatility3/volatility3/cli/text_renderer.py inside of the Volatility source code where the existing renderers are implemented.
Please note that framework-wide command line options, such as -r and ‐-filters, must be specified before the plugin name to take effect.
Consistent Data Extraction Configuration
Extracting files, processes, memory ranges, and kernel modules from memory with Volatility 2 required a bit of a learning curve, as each plugin was free to choose its own command-line option name, input format, and output structure. Volatility 3’s core architecture introduces a consistent interface for both plugin developers and users.
With Volatility 3, all core plugins that extract data are required to follow the file extraction API, which means the following:
-
Users can add -o before the plugin name to specify an output directory to write files. Otherwise, files are written to the directory from where Volatility was invoked.
-
All plugins that extract data take a single ‐-dump option.
Operating System Support
To support investigation of modern systems, Volatility 3 was developed and extensively tested (complete details later in this post) on a wide range of operating system versions, including bleeding-edge releases. This support is ongoing, and the Volatility Team will continue to fix bugs and add new features as operating system releases evolve.
Windows Support
Volatility 3 aims to support Windows XP through 11, and their Server release equivalents, for both 32- and 64-bit Intel systems. We note that many ancient kernels, such as early versions of XP and Vista, have broken and/or missing debug symbol files on Microsoft’s server, so some kernel releases from these versions are not supported. Given the age of these releases, we are hoping analysts do not encounter them too often, but we are painfully aware of their ongoing use in production environments.
Linux Support
Volatility 3 aims to support Linux 2.6.18 (release year 2008) through the latest versions as they are released. Given the pace of core Linux kernel changes, and the variety of distributions that make their own changes, we are not always perfect with this, so please file a bug on our GitHub tracker if you are testing against a bleeding-edge kernel and plugin(s) break.
We note that ARM support for Linux and Windows is in development, but there is currently no timeframe for its official inclusion given our team’s recent focus on achieving the parity release.
macOS
Apple has made a well-publicized and debated decision to lock third parties out of the kernel – at least those who want to enter through legitimate means. For this reason, memory acquisition of modern Apple systems in on-demand situations is not feasible. Having a system trust and load a kernel extension to collect memory requires significant setup (in advance) and at least one reboot of the system. For this reason, Volatility 3 does not support macOS.
Luckily, the acquisition roadblocks are less challenging in enterprise environments, since systems can be configured through MDMs to accept third-party drivers. This approach is currently used by many organizations to gain the vital capabilities of memory forensics on their critical macOS systems without disabling SIP or introducing new security risks. We recommend contacting Volexity for enterprise macOS memory acquisition solutions and analysis support for the latest versions of macOS.
Release Schedule
We intend to have ongoing, official releases of Volatility 3 every three to four months. This schedule may change if critical bugs are found in the framework, or if an operating system vendor releases updates that break a significant number of plugins or analysis workflows. Please see the end of this blog post for methods to follow news on updates.
The release page on GitHub contains all of the files and change log entries per release. This includes a Python wheel file, as well as the source code snapshot. Besides bug fixes, the change log also lists new plugins that were added since the last release.
Volatility 3 will remain under active development far into the future. If you encounter a bug in the latest release of Volatility 3, you should check to see if the develop branch of the GitHub repository has fixed the bug. The develop branch contains all the approved code changes to Volatility 3 since its last official release and will contain bug fixes applied since release.
Automated Testing
To detect analysis bugs before they are included in releases, and to avoid analysis regressions being added to the framework, Volatility 3 adopts several modern coding practices.
First, a series of automated tests are run on pull requests before they are allowed to be merged. We are constantly expanding these tests to provide better coverage; catch common, unintentional Volatility 3 API misuses; and enforce the coding standards. We accept contributions for further tests to meet these goals, so if you are a CI/CD expert, then please consider contributing more tests!
Second, before official releases are published, a full regression test against the previous release is performed. This regression test uses a set of ~500 Windows and Linux memory samples maintained by Volexity that covers an expansive variation of operating system versions; legitimate third-party applications; malware samples; open-source and private post-exploitation frameworks; and anti-forensics tools. This regression test aims to ensure Volatility 3’s stable support of artifacts and workflows throughout its lifetime.
Recent Recorded Conference Presentations on Volatility 3
Over the last two years, our team has been presenting Volatility 3’s new features and completely new research at a variety of conferences. We encourage you to watch these presentations as they will get you up to speed on modern investigation techniques, and show how Volatility 3 is being used in a variety of settings.
Highlights include the following:
Upcoming Events
Now that Volatility 3 has reached parity, we are hoping to present its latest features during talks and workshops at many upcoming conferences throughout 2025 and 2026. We have a few of these confirmed, along with several pending CFP submissions.
At the time of writing, the following are confirmed events:
-
A presentation at RVASec in June 2025
-
A workshop at DFRWS USA in July 2025
-
An Arsenal booth at Black Hat USA 2025 in Las Vegas
-
The Volatility Foundation’s FTSCon in October 2025 (more details in a new blog post very soon!)
If you are a conference organizer and would like to have us present or host a workshop at your event, then please let us know!
Want to Get Involved?
As mentioned in this post, we always encourage contributions from community members outside the core team. These contributions can take the form of new plugins, new architecture support, new automated tests, or any other useful feature.
Those who make these contributions should consider submitting them to our annual Volatility Plugin Contest for the chance to win prizes, such as free training seats, cash, and swag!
And for those who prefer not to contribute code, equally as important are the contributions to Read the Docs documentation, tutorials on using Volatility 3, triaging of bug reports, testing of new operating system versions, and helping us spread the word on new releases and features within your professional community.
Self-Paced, Online Training Updated
Since mid-2020, the highly popular course, Malware and Memory Forensics Training with Volatility, has existed in a self-paced, online format. We are now very happy to announce that this training course has been fully converted to Volatility 3! It includes significant updates that incorporate the latest attack and malware techniques along with recent research efforts. These new lecture sections and labs have expanded the course to cover a full six days of material (instead of the previous five days).
This training course teaches you not just how to use Volatility 3, but also the malware and operating system internals needed to fully understand how malware and attackers operate and the specific subsystems they abuse for their goals. Given the significant course overhaul to Volatility 3, the course has been revamped to make it easier for students to retake the course with the new content. So if you have ever taken the Volatility 2 version of the course, then please check the Training FAQs for the alumni discount. Also, if you have registered for the course since October 1, 2024, whether online or in person, then you are entitled to a free voucher to the new version.
All information on this course can be found on the official training site.
How to Stay in Touch and Follow Updates
There are many methods to follow project updates and to interact directly with the developers and community!
We have many exciting announcements coming soon, including information on our annual From The Source conference (FTSCon), our first in-person training of 2025, speaking events, and new Volatility 3 features. Be sure to follow us on at least one of the platforms above to keep up with all the latest updates!
Acknowledgements
We would like to sincerely thank our community, who has continued to support this project since 2008. As any software developer knows, a complete rewrite of this scale and size often fails. Finally getting Volatility 3 out the door was only possible because of the amazing community that continues to support and maintain the project.
In particular, it’s great to see the new generation of contributors who are ensuring that Volatility will continue to thrive into the future.
We would also like to thank Volexity for its continued support and resources.
Closing Thoughts
We hope that Volatility 3 continues to enable successful investigations and to inspire new generations of DFIR researchers.
As always, please come say hello if you see us at events, and we hope you can join us at our FTSCon this October! (Watch for that blog post announcing details, coming soon!)
‐- The Volatility Team